POODLE (CVE-2014-3566)
Posted 28 Oct 2018
The Padding Oracle On Downgraded Legacy Encryption (POODLE) attack was published in October 2014 and takes advantage of two factors. The first is the fact that some servers/clients still support SSL 3.0 for interoperability and compatibility with legacy systems, and the second factor is a vulnerability that exists in SSL v3.0 which is related to Block Padding.
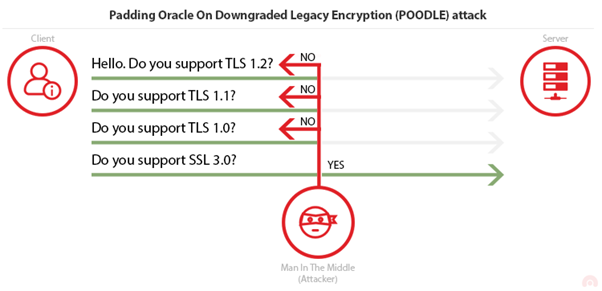
The Client initiates the Handshake and sends the list of the supported SSL/TLS versions. An attacker intercepts the traffic, performing a Man-in-The-Middle (MiTM) attack, and impersonates the Server until the Client agrees to downgrade the connection to the vulnerable SSL 3.0.
Now that the connection between Client and Server is established on a vulnerable SSL version, the attacker can perform the actual POODLE attack. The vulnerability exists in Cipher Block Chaining mode. Since Block Ciphers have fixed length, if the data in the last block is not a multiple of its size, then padding is added to fill the extra space. One of the problems is that padding value is ignored by the server and checks only if padding length is correct as well as Message Authentication Code (MAC) of the plaintext. That means the receiver (Server) cannot verify if padding value has been modified.
An attacker can decipher the plaintext value of an encrypted block by modifying the padding bytes and then seeing the corresponding response from the server. It takes a maximum of 256 SSL 3.0 requests to decrypt a single byte.
This means that once every 256 requests, the server will accept the modified value. The attacker does not need to know the encryption method or key to pull off this attack. Using automated tools, an attacker can retrieve the plaintext character by character. This could easily be a password, a cookie, a session or other sensitive data.
Prevention
- 1. Completely disable SSL3.0 on the server (Recommended)
- 2. Upgrade browser (client) to the latest version or if for whatever reason you need to use an older version be sure to disable SSL 2.0 and SSL 3.0 Protocols. Most up to date browsers/servers use TLS_FALLBACK_SCSV. If a client requests a TLS protocol version which is lower than the highest supported by the server (and client), the server will identify intentional downgrade fallback and will drop the connection.
- 3. Some TLS 1.0/1.1 implementations are also vulnerable to POODLE as they accept incorrect padding structure after the decryption.

