Heartbleed (CVE-2014-0160)
Posted 29 Dec 2018
Heartbleed was a simple to exploit, critical vulnerability found in the heartbeat extension of the popular cryptography library OpenSSL. This attack takes advantage of the TLS heartbeat extension which is primarily used as a keep-alive method between two parties to and ensure that the connection is not closed if they are both still there.
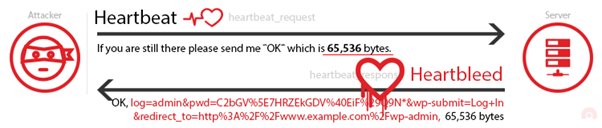
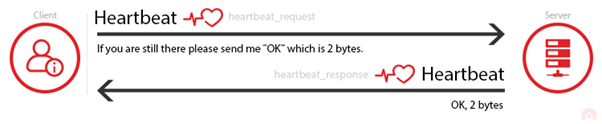
The heartbeat request works as follows. The client sends a “heartbeat” message to the server with a payload which contains data+size of the data (and padding). The server must respond with the same “heartbeat” request, containing the data+size of data that the Client sent.
The problem was that, if the client sent false data length, the server would respond with the data received by the client + random data from its memory to meet the length requirements specified by the sender even though the data was smaller than the specified length.

Having the server leaking un-encrypted data from its memory can be disastrous. There have been proof-of-concept exploits of this vulnerability in which the server’s private key leaked through the Heartbleed vulnerability. This means that an attacker was able decrypt all the traffic of the server with anything this may imply. In the server’s memory, there could be anything sent to the server for encryption such as credentials, sensitive documents and emails.
Prevention
Update to the latest version of OpenSSL and if that is not possible, recompile the already installed version with -DOPENSSL_NO_HEARTBEATS

