CRIME (CVE-2012-4929)
Posted 5 Dec 2018
Compression Ratio Info-leak Made Easy is a vulnerability found in TLS compression. The compression method, is included in the ClientHello message and it is optional, meaning that the connection can be established without any compression.
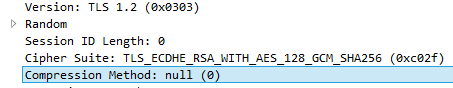
This is a Wireshark capture of a ServerHello message (response to ClientHello), selecting NULL compression method which means that no compression will be used.
Main purpose of this feature (compression) is to reduce the bandwidth usage while preserving integrity (lossless data transfer) and security when exchanging large amounts of information. DEFLATE is the most common compression algorithm used.
One of the main techniques used by compression algorithms is to replace repeated bytes (characters) with a pointer to the first instance of that byte. The more the repetition, the higher the compression ratio.

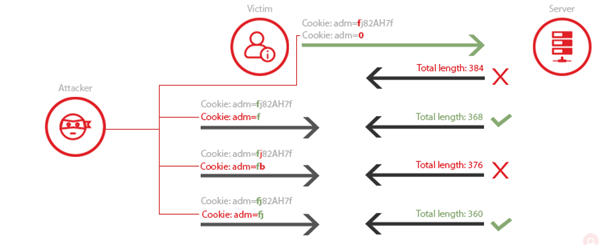
Let’s assume that the attacker wants to get a victim’s cookie. They know that for the session, the targeted website (examplebank.com) creates a cookie named “adm”. Having established that DEFLATE compression method replaces repeated bytes, if the attacker injects Cookie:adm=0 into the victim’s cookie, the server will append only 0 to the compressed response since Cookie:adm= is already sent in the victim’s cookie, therefore repeated.
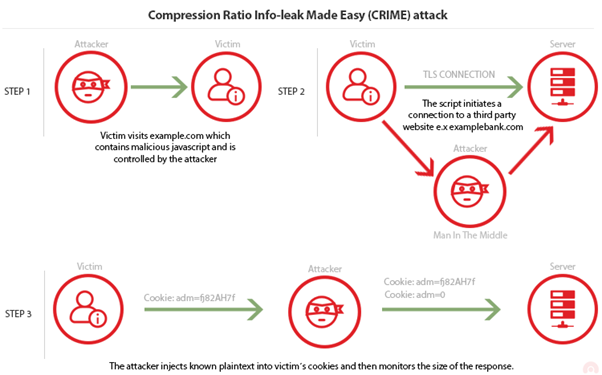
All the attacker must do is inject different characters and then monitor the size of the response. If the size of the response is lower than the initial it means that the character they injected is contained in the cookie value and thus got compressed, which equals to a match. If the character is not in the cookie value, the size of the response will be larger.

Using this method an attacker can essentially bruteforce the cookie’s value using the feedback they get from the server.
Prevention
Upgrade browser to the latest version

